security
🔒
This article is a stub. You can help the IndieWeb wiki by expanding it.
security in the context of the indieweb may refer to security concerns regarding personal domains, web hosting, https setup, private data, identity etc. Nearly everything on the internet, including the web, and thus indie web, has security concerns.
Why
Security is not a simple thing that's acquired. It's sometimes referred to as a process. We as site owners ought to take reasonable steps to keep the parts of our sites, DNS, hosting, to build trust with site visitors.
Web pages are often static, but as site owners add capability--for example webmentions or comments--pages are more like software: "web applications." OWASP (Open Worldwide Application Security Project) is a nonprofit foundation that works to improve the security of software and maintains the OWASP Top Ten.
But in general hosting companies often make recommendations about the management of the resources on a website to keep things secure.
How to
See:
- CSP
- HTTPS
- sandbox
- Open Worldwide Application Security Project (OWASP) is a non-profit that provides free resources, research, and tools for web application security
Visibility
Services that require logins or act as authorization servers should provide a way for users to see an audit trail of events relating to their account. For example:
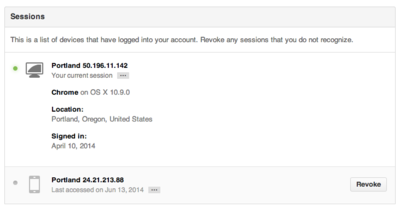
GitHub Security History
GitHub provides a page listing accesses to your account with details such as from what device, OS, location, date of access:
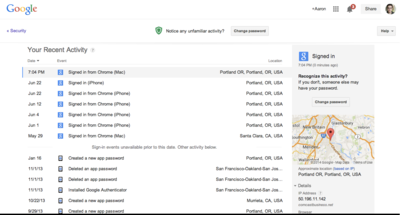
Google Recent Activity
Google provides a security recent activity log with date, browser, OS used to access your account and other information:
Breaches
Security breaches as reported by sites
2014
- 2014-04 Heartbleed
- 2014-02-15 Kickstarter https://www.kickstarter.com/blog/important-kickstarter-security-notice
- ...
Reproducible problems
https http botches
Today, when standards like HSTS try to mitigate https to http degradation attacks, there's no reason to allow http at all. All http should redirect to https. Examples of "willful degradation" in indie web related software and services:
- Webmentions to Known only work if you mention the http URL. This may encourage using unsafe links to Known (that shouldn't exist in the first place).
- webmention.io regards http and https as different URLs. Perhaps this is not a bug, because in a perfect world there wouldn't be any https.
Web Hosting
Should you write about your web hosting setup?
In some regards yes, to help out other members of the community.
However from a security perspective, disclosing what web host you use, software, VPS, or how you implement your server configuration are potential security issues because every piece of information you give a potential attacker about your setup helps narrow the space of weaknesses to explore.
So, how do you share information without endangering yourself in that regard?
You decide you're not a worthy target, or you decide you'd rather share publicly in the hopes that friends will warn you about any flaws before an attacker exploits them.
Dealing with unknown problems
Per https://en.wikipedia.org/wiki/Secure_by_design :
- Peer review existing protocols and implementations.
- Look for docs, advice, potential peer-reviewers at communities like MIT's Liberationtech mailing list (any other ideas?).
- Think in advance about security implications of features like private messages.
- Always prefer existing and popular (i.e. constantly peer reviewed) technology to reinventing crypto.
- Eventually - prepare guidelines for site owners and developers on the Wiki (similar to Eff's SSD).
See Also
- CSP
- https
- WordPress_Security
- https://securityheaders.io/
- https://medium.com/@david.gilbertson/im-harvesting-credit-card-numbers-and-passwords-from-your-site-here-s-how-9a8cb347c5b5
- 2016-11-09 How to encrypt your entire life in less than an hour
- https://security.googleblog.com/2019/05/new-research-how-effective-is-basic.html
- 2019-05-25 NYTimes: In Baltimore and Beyond, a Stolen N.S.A. Tool Wreaks Havoc
… vulnerability in unpatched software that allows hackers to spread their malware faster and farther than they otherwise could.
- Follow-up 2019-05-31: Ruppersberger: NSA has no evidence EternalBlue was in Baltimore attack - N.S.A., in briefing with Baltimore Rep. Dutch Ruppersperger, says no evidence that EternalBlue was used in the Baltimore ransomware attack.
- 2019-06-04: Violet Blue Cybersecurity Roundup for June 4, 2019 lays out exchanges between NYT author and security researchers. (see "Uh, enjoy the show?" section).
- 2022-03-21 Whitehouse.gov: FACT SHEET: Act Now to Protect Against Potential Cyberattacks (good advice for all developers)
- 2025-052
 Tantek Çelik: CSF_01: Three Steps for IndieWeb Cybersecurity
Tantek Çelik: CSF_01: Three Steps for IndieWeb Cybersecurity